With the adoption of cloud data centers, organizations are now able to scale their applications at reasonable costs. Most cloud platform infrastructures are serverless – meaning the cloud platform provider manages and maintains the IT infrastructure systems. Therefore, security teams focus more on functioning tasks rather than IT operations. As a result, operational processes are reduced, creating security issues and increasing the attack surface.
About Amazon Web Services Microservices Architecture
A Microservice architecture is a structural and operational gate to software development, to expedite deployment cycles, promote innovation and scale software systems. This approach to application development builds web applications as a series of modular services. A container service is a great fit due to their seclusion, allowing flexibility, resource density and portability.
Microservices architecture allows the continuous deployment of larger applications, enabling organizations to constantly develop their technology expansion. In Microservices, presentation and logic tiers are usually connected, bringing many benefits to the overall architecture, but they can also increase security concerns.
Building AWS Microservices architecture with containers can reduce disparities between development and production, facilitating unceasing deployment for ultimate agility. A productive way to achieve a clean contract with the operating system in AWS services is by defining the limits for services unique to your AWS cloud application’s design. The Microservice can be tracked in a data management control system, making it easy for companies to host secure and highly scalable private Git repository.
Building Microservice Architectures for an AWS Environment
In a Microservice architecture, each request for the application generates an API clone. Moreover, every time an API is processed, a new command of the logic tier is instigated, with the opportunity to process several calls from each API clone.
When threat modeling for AWS, the difference between applications developed for a Microservice environment and a deployment environment is insignificant. An application developed for a Microservice architecture becomes the deployment environment. Identifying threats and vulnerabilities for that type of application can be different than doing it for traditional applications, requiring a different approach to threat modeling for AWS.
Additional Benefits of Microservice Architecture
Each Microservice has its own approach on data management. Systems can be scattered in the way they are developed, deployed, managed, and operated. Using AWS Microservices can help with auto scaling web applications and operating systems while improving both development and deployment processes. Here are some of the added benefits of using Microservice architectures:
Agility
Agile processes executing web application life-cycle management processes from committing to releasing code can be automated. It is then easy to test new ideas and to step back in case something doesn’t work.
Easy Deployment
The divided nature of Microservices encourages organizations of small autonomous teams that control their service. They are qualified to easily develop and deploy independently and in parallel to other teams, which speeds up both development and deployment processes.
Reusable Code
Utilizing Microservices can improve the quality of code. The reduced intricacy of the code and the lower number of dependencies minimizes code errors, speeds up change, reduces test cycles, and ultimately improves the time to market for new features and services.
Scalability & Resilience
Auto scaling processes are completely automated, therefore, the resiliency of the web application can be improved in real-time since failing components can be easily and automatically replaced.
Threat Modeling for AWS
Threat modeling is the best approach to understand threats and risks unique to your application in cloud-native architectures. When implementing threat modeling for AWS or other serverless cloud environments, a 3-tier architectural pattern is typically utilized. The three tiers are the presentation tier, logic tier, and data tier. The presentation tier operates as the user interface and it’s created by the API gateway. The logic tier drives the application’s behavior and the data tier is where data is stored.
Learn More: Creating a Basic AWS Cloud Threat Model
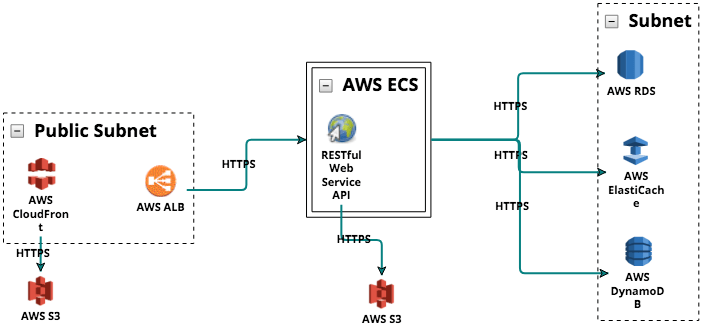
How to Secure Microservices
The above image shows a threat modeling diagram for AWS deployed in a Microservices architecture employing ThreatModeler. This application allows registering and authenticating users, recovering user passwords and providing fundamental feedback of user file uploads.
The presentation tier was presented as cloned AWS API gateways within a public subnet. The AWS-specific architectural components in ThreatModeler are pre-mapped to AWS-specific threats. The logic tier in an AWS serverless environment is formed around their Lambda service. In a Microservice deployment, the logic process for each application is described as a separate Lambda function.
When building an AWS threat model, only one proper Lambda functioning is required for each application to function properly. However, a Microservice architecture will call as many clones of each function to serve calls from API gateways.
ThreatModeler provides users with prebuilt architecture components and templates applicable to AWS environments. It can take 10-15 minutes to build the above threat model by employing ThreatModeler.
Additional Considerations for Microservices Architecture Security
One of the primary challenges with Microservice architectures is building a secure system free of threats or risks. AWS resources offers a wide array of managed services that help product teams to build Microservice architectures and reduce the attack surface of applications.
In a Microservice architecture, the means of monitoring custom metrics using Amazon CloudWatch is an additional benefit. Developers can decide which metrics to collect for each service. In addition to that, dynamic scaling can be implemented based on custom metrics. Consistent logging is critical for troubleshooting and identifying issues. Microservices allow the production of many more releases than ever before and encourage engineering teams to run experiments on new features in production. Understanding customer impact is crucial to improving an application gradually.
Storing logs in one central place is essential to debug and get an aggregated view on distributed systems. In AWS you can use Amazon CloudWatch Logs to monitor, store, and access your log files from Amazon Elastic Compute Cloud (Amazon EC2) instances, AWS CloudTrail, or other sources. Amazon EC2 includes support for “awslogs” Log Driver that allows the centralization of container logs to CloudWatch Logs. There are different options to centralize your log files. Most AWS services already centralize log files out of the box.
The primary destinations for log files on AWS are Amazon S3 and Amazon CloudWatch Logs. Log files are a sensitive part of every system, almost every process on a system generates log files. A centralized logging solution aggregate all logs in a central location in order to have the ability to search and analyze these logs using tools like Amazon EMR or Amazon Redshift.
In many cases, a set of Microservices work together to handle a request. Imagine a complex system consisting of tens of Microservices. Now imagine an error occurs in one of the services in the call chain. Even if users properly log each Microservice and consolidate logs in a central system, it can be very hard to find all relevant log messages.
Automated Threat Modeling For AWS Services and More
ThreatModeler is an automated threat modeling tool that strengthens an enterprise’s SDLC by identifying, predicting and defining threats across all applications and devices in the operational IT stack. This automated platform works with all types of computing environments.
To learn more about how ThreatModeler™ can help your organization build a scalable threat modeling process, book a demo to speak to a ThreatModeler expert today.