Telecom networks tie together and coordinate activity between other critical infrastructures, businesses, government agencies, and individuals. In our highly interconnected cyber ecosystem, virtually everyone relies on telecom networks for “always on” services.[1] Without telecom networks operating, the economy will come to a screeching halt. Real-time situational awareness of the threat environment and level of telecom network security is critical for ongoing operational resiliency.
There are a number of persistent and emerging threats that continue to increase cybersecurity risk within the telecommunications industry. Typically, two types of cyberattacks occur – those targeting telecommunications network operations and indirect attacks, which seek to compromise subscriber information. The most typical threats leverage time-tested attack vectors to target telecom operators. With new technology, come new twists in complexity and scale. These types of hacks requires telecom network security teams to stay updated, plus stay abreast of new threats and vulnerabilities.
The following attacks seek to take advantage of not only time-tested telecom operator security vulnerabilities, but also attack surfaces within new technology, e.g. the Internet of Things (IoT).
Challenges to Telecom Network Security
Telecom network security is particularly challenged by cybercriminals and other threat actors with easy and inexpensive access to dedicated tools for attacking the telecom networks. Moreover, with the rapid growth of digital demand and the IoT, market forces have driven telecom operators to transform from physical network companies to cloud service providers.
As a result, telecom companies’ attack surface and cyber risk exposure increase significantly, as do the frequency of cyber attacks. Once a threat actor gains access to the network, they can steal confidential data or insert malware on specific downstream customer networks, or conduct a DDoS or other broad-based attack designed to disrupt broad geographical swaths of the economy, put large numbers of people in harm’s way, or simply cause large-scale mayhem.
Because of the critical role of communication networks, Presidential Policy Directive 21 identifies them as a critical infrastructure. However, unlike other critical infrastructures, it is the telecom companies themselves, not the federal government, who are responsible for telecom network security.
The federal government holds these service providers responsible to identify threats, anticipate attacks, and proactively mitigate the risks of service disruption or other attacker activity. The only way to sufficiently understand the threats and threat actors, and to gain the real-time situational visibility needed for concrete proactive measures, is through the “big picture” perspective that enterprise threat modeling provides.
Emerging Telecommunications Security Threats
Within the following common threat scenarios, hackers compromise infrastructure through vulnerabilities and gaps in telecommunication security. IT systems, applications and networks, for example, become particularly vulnerable to cyberattacks when access controls are poorly configured, or Wi-Fi networks are inadequately secured. Hackers target networks, and manipulate human behavior such to orchestrate insider access, social engineering and third-party access to sensitive information.
User Authentication Hacking
Authentication is a vital part of telecommunication security, in which a person verifies that s/he is who s/he claims to be. An authentication mechanism grants authorized users access to systems and applications, typically with a username and password. Once in, users take advantage of privileges, e.g. resources, based on their roles and responsibilities.
There is a number of different protocols for authentication methods, the most basic being logon authentication with a username and password. Newer technology such as biometrics and captcha, serve as additional authentication approaches. With user authentication hacks, bad actors attempt to gain access to the login portal, then guess the user name or password. Cybercriminals may use some form of automation, such as with a Dictionary or Brute Force attack, to try multiple username and password combinations in a shorter amount of time.
Hackers may also search for firewall vulnerabilities, or use other forms of cyberattacks, e.g. man-in-the-middle and session eavesdropping, to lift login credentials during input.
SIP Toll Fraud Hacking
Telecom network provides that utilize voice over internet protocol (VoIP) render themselves vulnerable to the same security vulnerabilities that impact the internet. Cyber fraud involving VoIP targets go after telecom network customers. In the case of SIP toll fraud hacking, cyber criminals will attempt to bypass security measures, then use customer accounts to send expensive, long distance calls. Worldwide, the cyber threat of SIP tool fraud hacking ends up costing billions of dollars per year.
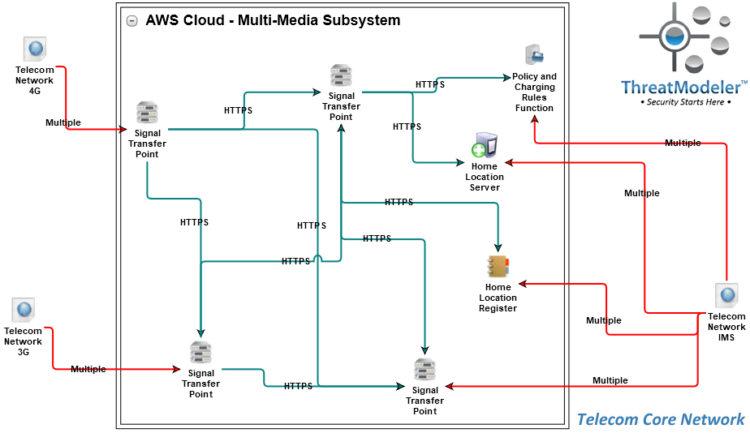
Modern telecom networks are comprised of multiple subsystems, shown above as chained threat models. As shown in this network architecture diagram, the telecom system for which we will build a threat model consists of a 3G subsystem, a 4G subsystem, and an IMS subsystem, all connected to and coordinated by a core system.
Modern telecom networks are comprised of multiple subsystems, shown above as chained threat models. As shown in this network architecture diagram, the telecom system for which we will build a threat model consists of a 3G subsystem, a 4G subsystem, and an IMS subsystem, all connected to and coordinated by a core system.
Telecom Network Security Solutions ThreatModeler™
The Core subsystem is comprised of an interconnected network of Signal Transfer Points. These are large-volume routers that receive incoming signals and transfer the outgoing signals to the appropriate subsystem. Signal transfers are managed by the Home Location Server which draws from a Home Location Register database.
The register contains the physical location of each telecommunications endpoint in the local network’s service area – including the location of mobile devices. We will also include in our core network the Policy Charging and Rules Function. The PCRF helps the network provider differentiate services while maximizing revenue.
The above threat model, along with the three chained threat models, identified 342 potential threats and 171 security requirements. You can download the summary threat model report here.
If you would like to learn more about how enterprise threat modeling with ThreatModeler can help you develop better telecom network security, then schedule a live demo today.
[1] Ben-Shimol, Snir. “Today’s Cyber Security Threats in the Telecom Industry.” Radware Blog. Radware Ltd: Tel Aviv. March 23, 2016.