For four years, running cybersecurity and interconnected infrastructure have topped the list of risk sources, according to the results of the 11th Annual Survey of Emerging Risks.[1] Risk sources considered in the survey include climate change, asset price collapse, financial volatility, regional instability terrorism and wars, weapons of mass destruction, and other large-scale disruptive factors. Cyber risk, however, is a unique component of an organization’s overall risk portfolio.
Multiplying Sources of Cyber Risk
Cyber risk is defined as the potential for any financial loss, disruption, or damage to an organization’s reputation from any manner of IT system failure.[2] While this is an inclusive definition, the primary concern for most organizations will be related to the security of their digital assets.
That cyber risk arises from digital assets is no surprise. Digital assets are, by nature, transitory and volatile. They may be copied an indefinite number of times, deleted, or transferred around the globe in a moment’s notice. They can be combined, filtered, analyzed, or otherwise operated upon to create new and unique digital assets.
Securing what cannot be locked in a vault, conveniently tagged, or easily registered is a challenge. A list of customer addresses and names with associated purchasing history cannot be readily exchanged for groceries. However, with that information, marketers and cyber attackers can develop successful and very profitable campaigns.
There is more to Cyber Risk than Data Security
We all readily acknowledge that the potential for a data breach is a source of cyber risk. A loss of confidential information may expose the organization to significant regulatory consequences, especially once GDPR comes online this May. Moreover, the collateral damage from a data breach can expose the organization to additional financial losses and reputational damage. Hence, organizations invest significant resources in preventing data loss. Data security, though, is merely the low-hanging fruit to mitigating cyber risk. Effective data security – and reducing cyber risk exposure – requires securing the organization’s infrastructure.
There was a time, back in the 70s and 80s, when securing the infrastructure was mostly a matter of physical security. Locked doors, security guards, and cameras were the first line of defense. Of course, security teams also had to be ever vigilant against individuals manually inserting malicious code or walking out the door with unauthorized data downloads.
Today’s infrastructures, though, are highly interconnected. A successful attack on one organization may expose interconnected organizations through lateral movement.[3] According to researchers, there are five stages in a network attack: infection, compromise, recon, credential theft, and lateral movement. Once the new network is exposed, the attacker then repeats the five-step process.
Side-Stepping Network Detection
The most obvious response to the possibility of attack through IT system interconnectivity is to employ one or more levels of intrusion detection. Intrusion detection systems (IDS) work by predicting how incoming traffic will change the host state. A host-based intrusion detection system (HIDS) will be used to enforce endpoint security, defend against privilege escalation or malware, and so forth. A network intrusion detection system (NIDS) will scan network traffic for abnormal or malicious traffic in violation of the organization’s security policy.[4] An attacker looking to side-step an IDS during lateral movement will focus on confusing its ability to predict state change.
If the attacker can utilize fragmentation techniques, the overlapping IP fragments and TCP sequences can become the lateral movement bridge the attacker needs. Differences in how the IDS and targeted end host reconstruct messages can allow the attacker to move from the infected system to an interconnected system. Carefully crafted packages, once reconstructed, can yield traffic the IDS ignores while creating malicious traffic on the new host.
The Means to an Attacker’s Ends
Several publicized means for side-stepping network detection exist that will allow an attacker to migrate laterally migrate from an infected system to an interconnected one:
- Time to Live Manipulation – By manipulating the TTL field in an IP header an attacker can desynchronize the targeted end host from the IDS guarding it. If the attacker is successful in distorting the information the IDS uses, the defensive technologies will stop the bogus packets but allow the real attack packet through.
- IDS MAC Address Attack – Modern switches usually forward packets only to the host specified by the MAC address in the frame header. Hosts, unless explicitly configured otherwise, only process frames addressed to them. By crafting a packet with the MAC address of the IDS and the IP address of the targeted host, the attacker can desynchronize the IDS and host.
- IP Fragmentation Attacks – Different communication protocols have differing allowable packet and frame sizes. Seamless point-to-point communication requires the message be broken down – or fragmented – into the largest chunks that can be passed over the full communication path. For example, the maximum Ethernet frame size is 1,518 bytes. IP packet sizes can be as large as 65,535 bytes. IP over Ethernet requires the IP packet to be fragmented to fit into the underlying Ethernet frame size. Fragmentation attacks focus either on reassembly of fragments or on preventing fragmentation from taking place. In either case, the IDS and the host system are desynchronized, causing the IDS to lose track regarding whether the network traffic was discarded or passed to the targeted end host.
- Encryption – If network traffic is encrypted, as is increasingly the case for passed malware, the IDS cannot inspect traffic unless it has the decryption keys. IPSec-encrypted network traffic can be detected with entropy methods, but doing so will produce significant levels of false positives. In most cases, decryption will be beyond the capabilities of the IDS.
- Polymorphic Blending Attacks – Polymorphic attacks seek to evade signature-based IDS by changing the message signature through encryption, substitution, obfuscation, or other transformative techniques. A polymorphic blending attack is an advancement that also keeps byte frequency distributions and other behavioral profile variables within the acceptable range of behavior-based IDS.
Securing a single network connection against an attacker seeking lateral movement utilizing the above methods would be challenging enough. Attempting to secure against lateral movement in today’s highly interconnected cyber ecosystem, however, is another matter. Even a well-resourced OpSec team would be quickly overwhelmed without proper prioritizing of limited resources.
Understanding Interconnected Infrastructures like an Attacker
Effectively prioritizing defensive and security resources require understanding your IT system from the perspective of attackers. That, of course, is the purpose of threat modeling.
Most threat modeling processes can give insight into what an attacker could do against a web application. Understanding how an attacker could laterally migrate through the highly interconnected cyber ecosystem, however, requires enterprise threat modeling.
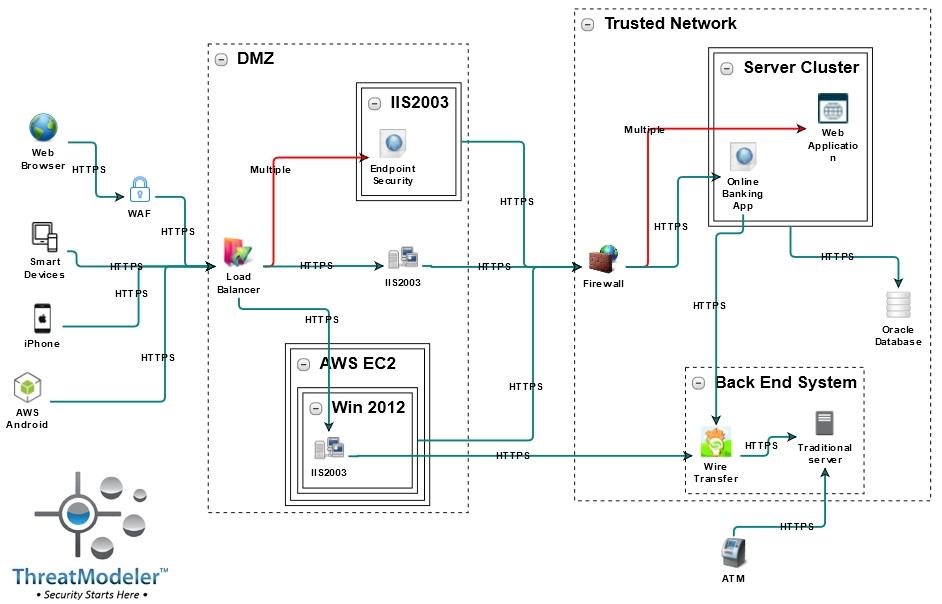
Consider, for example, a hypothetical banking infrastructure threat model:
This threat model shows how outside users – or attackers – access the Online Banking Application in the Trusted Network Server Cluster through one of several web servers in the DMZ. Once an attacker reaches the Online Banking Application, it is possible that he could initiate a data breach or force the Back End System to carry out a malicious instruction set. The cyber risk associated with a potential information data breach or malicious instructions to the Back End System can be mitigated through secure coding and the use of compensating security controls.
However, what if an employee downloads from a malicious website or a phishing email a malware package disguised as a PDF. The malware now has access to the DMZ system – before the firewall protecting the Trusted Network and behind the WAF filtering web traffic. Once the attacker completes recon on the DMZ portion of the bank’s network, he will have the access he needs to move laterally into the Wire Transfer system – a 3rd party vendor network.
From the perspective of the security team for the Wire Transfer service, understanding how attackers could infiltrate their network through their connectivity with the bank infrastructure is vital to prioritizing the necessary security resources. If cyber risk from a polymorphic blended attack is indicated by the threat model of the interconnected infrastructure, for instance, the security team can assume its existing signature-based IDS will be ineffectual.
Reduce Cyber Risk – Threat Model with ThreatModeler™
ThreatModeler is the Industry’s most advanced, automated threat modeling platform. With it, organizations can efficiently scale their threat modeling practice across hundreds or even thousands of applications, their full operational environment, and the myriad of connections that exist within their cyber supply chain.
Moreover, ThreatModeler™ comes out-of-the-box with more than 700 pre-defined threat definitions. The pre-defined threats include those designed to defeat IDS systems and allow attackers to migrate between systems. By understanding how attackers can laterally migrate from trusted networks disguised as normal traffic, security teams can obtain the resources and deploy the security controls need before the cyber risk is realized.
Reducing an organization’s cyber risk exposure from interconnected infrastructures begins with real-time situational visibility afforded through enterprise threat modeling with ThreatModeler™.
Schedule a live demo to learn more about how ThreatModeler™ can help your organization reduce cyber risk from interconnectivity.
[1] Rudolph, Max J. 11th Annual Survey of Emerging Risks. Society of Actuaries: Schaumburg. April, 2018.
[2] “Cyber Risk and Risk Management.” Institute of Risk Management: London. 2018.
[3] Heller, Michael. “Network lateral movement from an attacker’s perspective.” TechTarget: Newton. September 28, 2017.
[4] Gibbs, Pierce. “Intrusion Detection Evasion Techniques and Case Studies.” SANS Institute: North Bethesda. January 17, 2017.